CSRF Defence - Synchronizer Token Pattern Demo
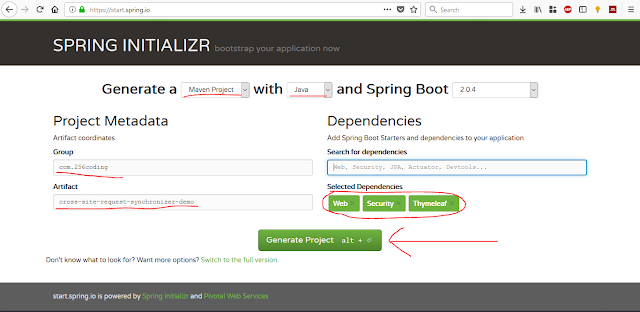
I have wrote some theoretical background of CSRF and CSRF prevention mechanisms in previous posts. If you don't have much idea about what CSRF and how prevention mechanisms works, please go back and read them first. These are the links for them. Cross Site Request Forgery (CSRF) CSRF Defence - Synchronizer Token Pattern From here onword, I assume you have the basic idea of concept of CSRF attack and prevention mechanisms. So, lets get started. This post is fully practical based one. At them end of this, There will be fully functioning web based application to demonstrate how CSRF attack works and how to prevent it using synchronizer token pattern. So, in order to follow this, you will need to setup your development environment first. These are the technologies I used to develop this demonstration application. Technologies Java 8 Spring Boot Framework Spring Security Maven Bootstrap 4 (Optional, Just for enhance the look and feel) Integrated Development Environmen...


